Here are a few notes I took while attending my first DockerCon – with some Docker-fan SoftwareAG colleagues – DockerConEU 2017, that happened October 16 -19 2017
All DockerConEU 2017 videos are online now !
Contents
- 1 Day 1 / Tuesday 17th of October DockerConEU 2017 General session
- 2 Day 2 / Wednesday 18th of October DockerConEU 2017 General Session 2
- 3 Play With Docker inside / out by Jonathan Leibiusky and Marcos Lilljedahl (Docker inc.)
- 4 Linuxkit Deep Dive by Rolf Neugebauer and Justin Cormack
- 5 My journey to go by Ashley McNamara
- 6 Modernizing Traditional Apps : Java edition by Sophia Parafina (Docker inc.) and Arun Gupta (AWS)
- 7 Containerizing hardware accelerated applications by Chelsea Mafrica (Intel)
- 8 Looking under the hood : containerd by Scott Coulton
- 9 Taking Docker to production : what you need to know and decide by Brett Fisher
- 10 Final notes / the end !
Day 1 / Tuesday 17th of October DockerConEU 2017 General session
You can find the video on this livestream (you’ll need to fill in a form though)
The new CEO, Steve Singh, went on stage for the first 30 mn, inspiring the audience with what was done until now and more to come.
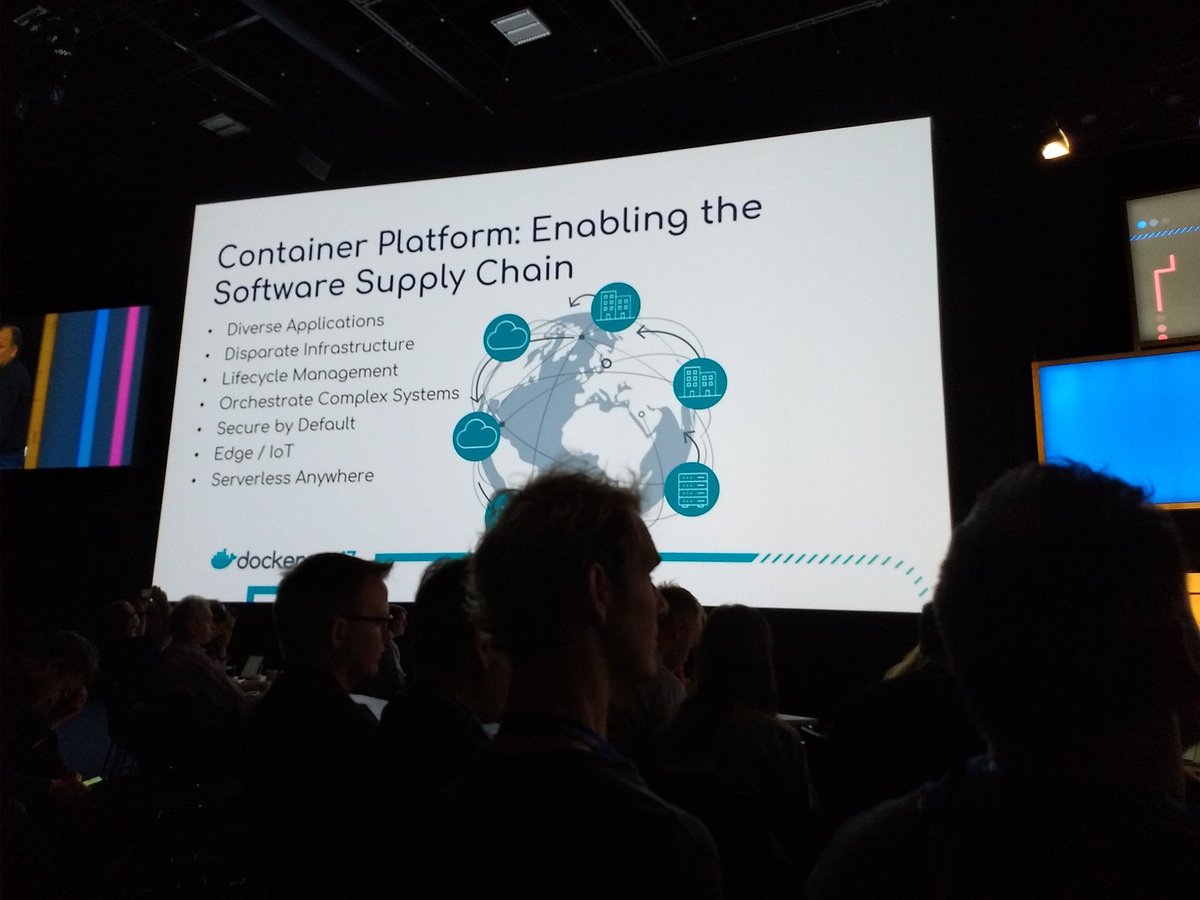
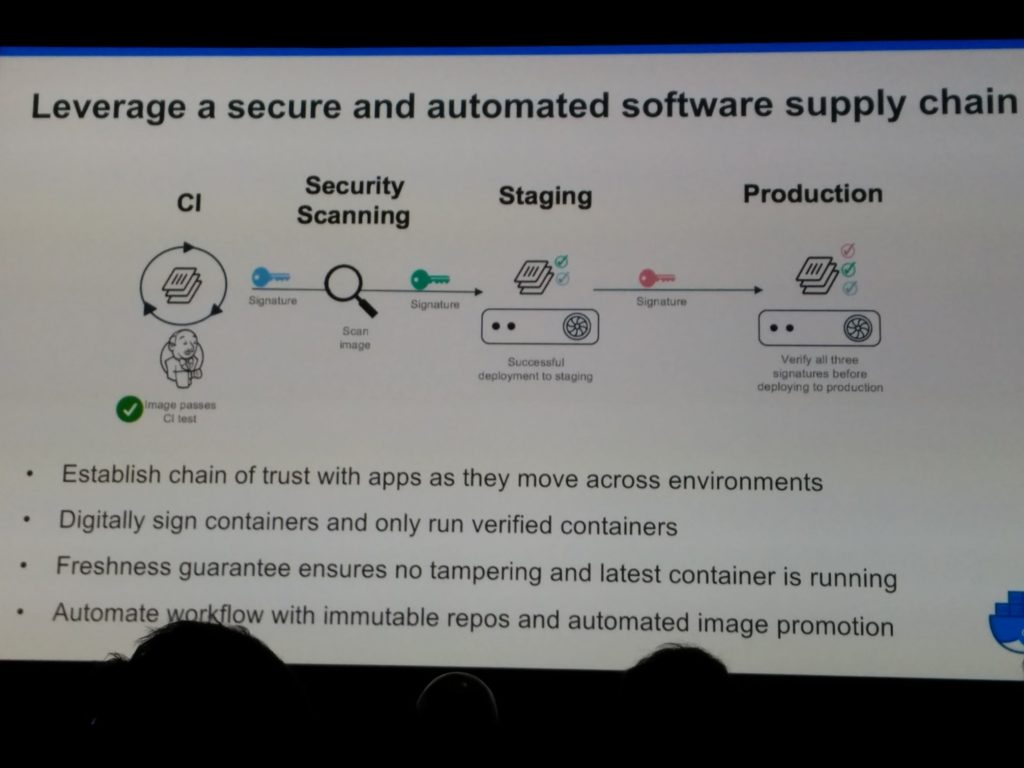
He went on describing the software supply chain…
…and MTA (Modernizing Traditional Apps) – MTA was definitely one of the main messages Docker Inc. pushed to the audience during the conference !
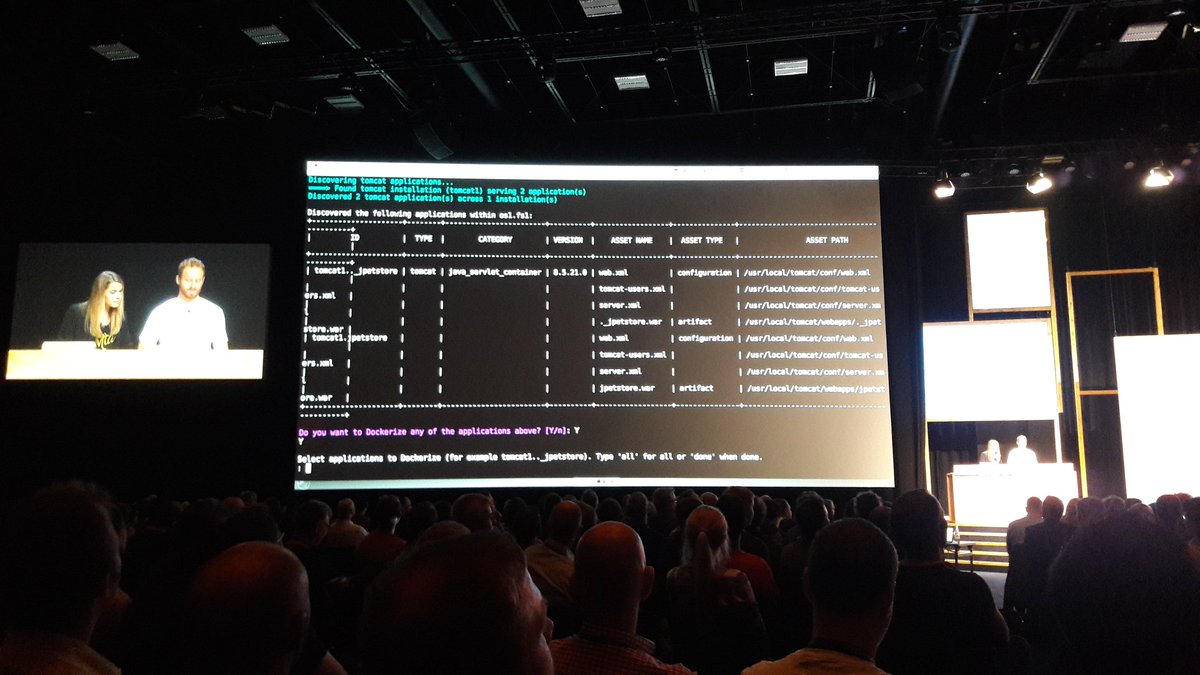
The first demo was about the DAC (Docker App Converter, should be shipping publicly end of 2017) : the engineers on stage converted an old Java War based application into an image deployed to the cloud.
Then a second demo continued the migration of the same Java based application, this time with orchestration, showcasing the Docker EE (UCP / Universal Control Plane) dashboard.
The orchestration was based on a Docker compose file, version 3.3, and was using secrets (secured password) and a secured network.
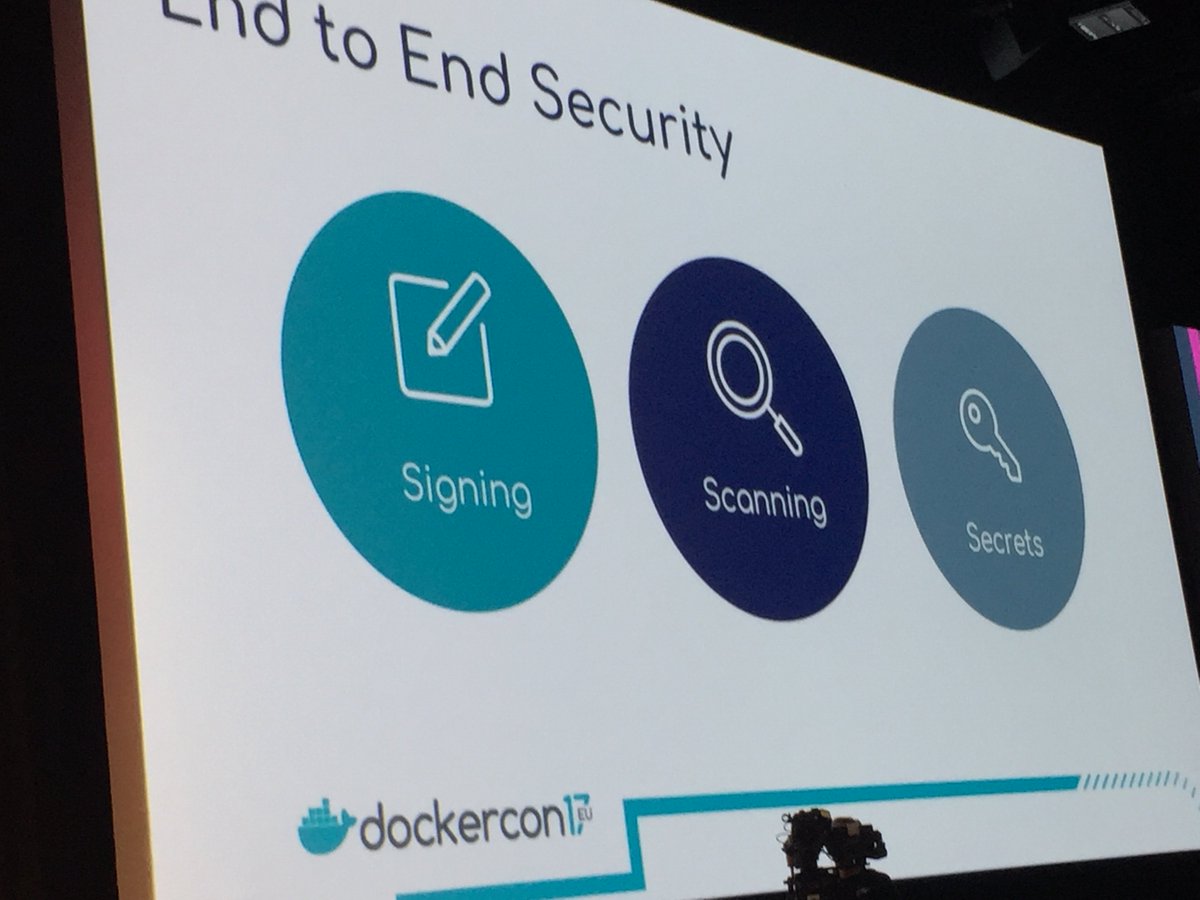
Then a senior PM introduced end to end security and enterprise multi tenancy.
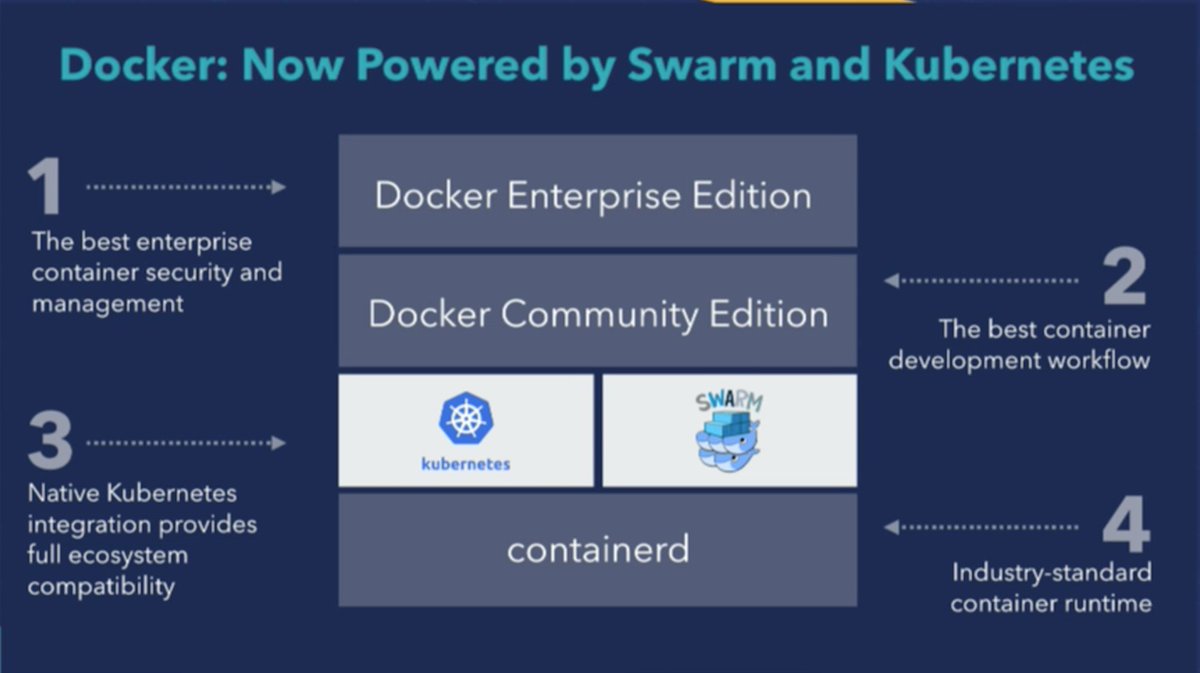
Then, it was Solomon Hykes turn to be on stage, he committed to an open community, and then explained the current vision of Docker Inc. (four layers)
And he announced the biggest news of the conference : dilemma solved for out of the box orchestration : swarm AND kubernetes are going to be both available when you deploy docker (it should be generally available –sign up here for the preview – by the end of the year for Docker4Mac, Docker4Windows, and Docker EE – it was not super clear what the pure Linux path is going to be, the Docker team is apparently figuring out how to handle updates gently…)
Then Brendan Burns, Kubernetes co founder working for Microsoft, went on stage and was happy to testify Microsoft is all about integration across platforms.
A demo of the Kubernetes integration was given by David Gageot, using docker stack commands to deploy to … a kubernetes cluster !!!
Docker Stack is now a first class citizen for Kubernetes, thanks to API Aggregation and Custom Resource Definitions; a linuxkit image with the original Kubernetes is being used for both docker and kubernetes.(no need for Minikube anymore on your laptop)
A few slides about Docker Enterprise edition were showed to the audience…
…with of course a demo of the kubernetes support : Kubernetes and Docker working together (kubectl can see Docker swarm nodes and interact with them, and vice versa; Docker EE knows about Kubernetes concepts); Tim Hawkins from Google was on stage to demonstrate that.
Day 2 / Wednesday 18th of October DockerConEU 2017 General Session 2
Docker COO put great emphasize on the necessity of fast delivery and MTA.
A demo showed a « docker trust sign » command, with the use of a private key password; Docker ee allows you to only run / deploy signed images by a certain group.
All the session was centered around MTA, and Docker partnerships (consultants and customers and cloud providers) – nothing technically interesting there.
Play With Docker inside / out by Jonathan Leibiusky and Marcos Lilljedahl (Docker inc.)
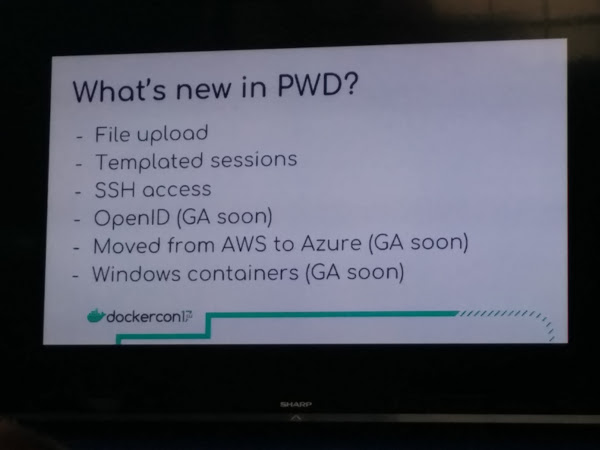
No doubt, this was one of my favorite sessions : this tool, http://labs.play-with-docker.com/ or PWD for the intimates, is really a gem !
What do its developers Jonathan and Marcos have to say about it ? « Biggest honeypot on the internet ! »
It runs Docker, even Docker Swarm, on shared Azure instances, via Docker In Docker (dind) – it allows anonymous people on the web to play with Docker.
During a demo they showcased drag n drop of files into PWD (for example you drop a docker compose file and you can deploy the stack right away)
User session is coming: no more captchas, you will be able to auth. with dockerid to keep your progress with labs. Windows containers were also introduced recently, providing the same experience.
The first challenge was about networking : first attempt with vpn, but it was hard to deal with windows VMs, so problem was solved on the linux hosts via iptables routing.
Second challenge was with the terminal : attempts with windows powershell and windows ssh, but ended up using nodejs pty because of slowness.
Public PWD is coming to other regions (currently west North America I believe), and alibaba cloud too.
It’s open source too : github.com/play-with-docker to run on your organization infrastructure.
Talking with the two presenters, I asked them if it was « secure » to login to his / her own docker account to pull private images (on dockerhub / or any other registry) from PWD; and they replied to me they would not recommend me to use the docker login directly in the browser, but that connecting through ssh and doing the docker login from my laptop would be safer, since my password would never be stored or known by PWD (just a token, so still a security risk).
Your best security bet with PWD ? hosting it yourself, it’s open source !
Linuxkit Deep Dive by Rolf Neugebauer and Justin Cormack
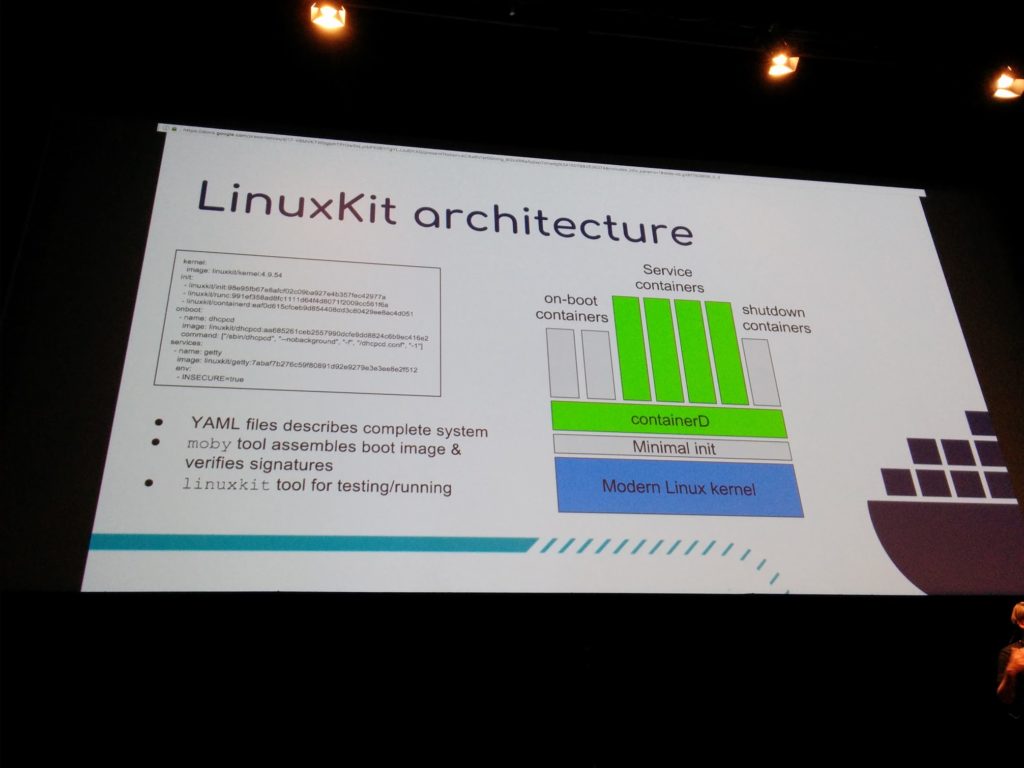
LinuxKit is a toolkit for building secure, portable and lean OSes for containers.
What’s new ? arm64 support, Kubernetes support, Linux Containers on Windows, and improved platform support.
During a demo Rolf built a linuxkit on x86_64, an arm64 server and a Raspberry PI3 using the same yaml build file and the same command line « moby build ».
Then he booted them using the linuxkit command.
Linuxkit base images are based on alpine and add several packages such as compilers, dhcp clients, etc. All the binaries will be run in containers with the minimum required kernel capabilities, to reduce the attack surface.
Linuxkit packages are signed and available on dockerhub (https://hub.docker.com/u/linuxkit/) – if you want to know more about signing images before pushing to the registry, you can read this article : https://mobyproject.org/blog/2017/06/26/sign-all-the-things/
Signing packages will be easier with « docker manifest » and « docker trust » commands (coming soon)
Justin of course talked about the most interesting recent addition, the Kubernetes inclusion
Finally, he introduced Wireguard : it’s a fast modern VPN included in linuxkit, that appears as a network interface, and allows you to pipe traffic into a secured channel.
My journey to go by Ashley McNamara
Not exactly a technical session, but a fun and refreshing one : Ashley is a photographer who became software developer at age 32.
She went through a code bootcamp, a terrible 12 weeks experience
She then created a popular Github page for developer resources.
Thanks to Steve Francia, she learned Go and gave several workshops about Go since then.
Ashley recommends people to not learn all alone, but to go out and find help.
The best project to contribute to is the one you’re already using.
She created gopherize.me ,the gophers repo (cute Go pictures) on GitHub.
She recommends developers to work with community (stack overflow, blog posts, open / close tickets and contributiion to docs).
Modernizing Traditional Apps : Java edition by Sophia Parafina (Docker inc.) and Arun Gupta (AWS)
Containers allow you to abstract applications (that sometimes you don’t have the source code anymore…) from infrastructure, they can also reduce the attack surface area.(see my notes on linuxkit for example, the base image generator for many Docker host deployments)
Docker compose files are the way to go to drastically simplify deployments (versus a set of Docker command lines)
Across staging, you can scan your images for vulnerabilities (usually though enterprise products such as … Docker ee !)
For the demo, they used a lab : https://dockersamples.github.io/dceu-labs/java-mta/ ; it’s pretty cool to follow through, it’s based on Play With Docker, no need to install anything on your machine, it’s only going to take you 10mn of your time, I highly recommend this lab !
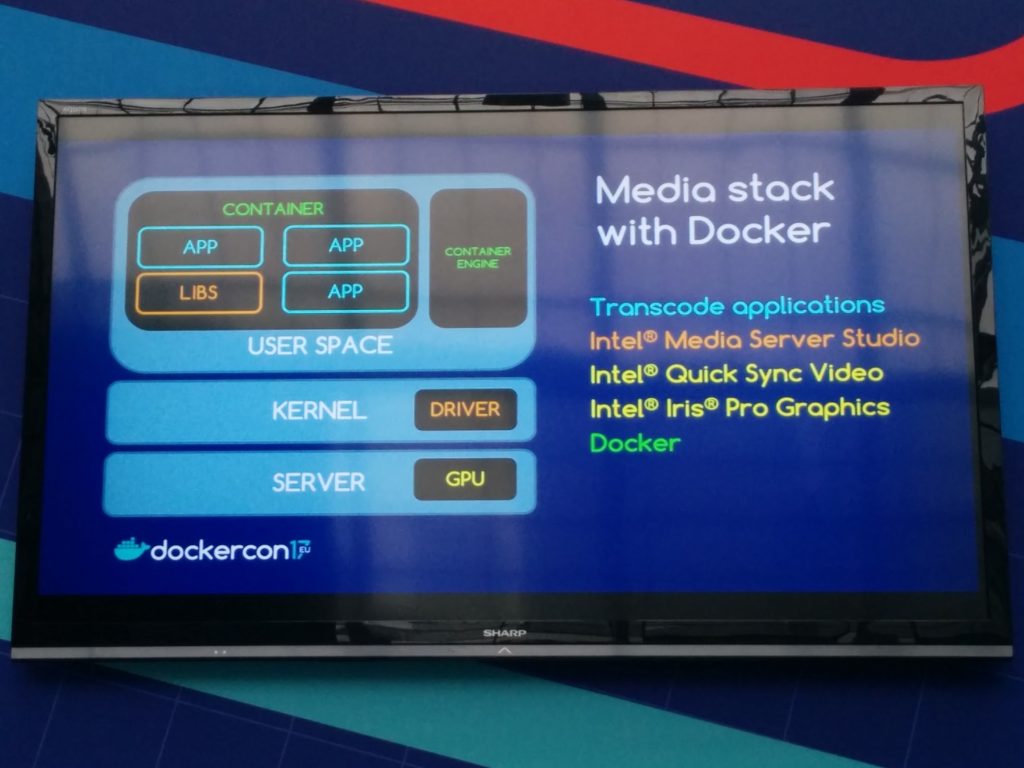
Containerizing hardware accelerated applications by Chelsea Mafrica (Intel)
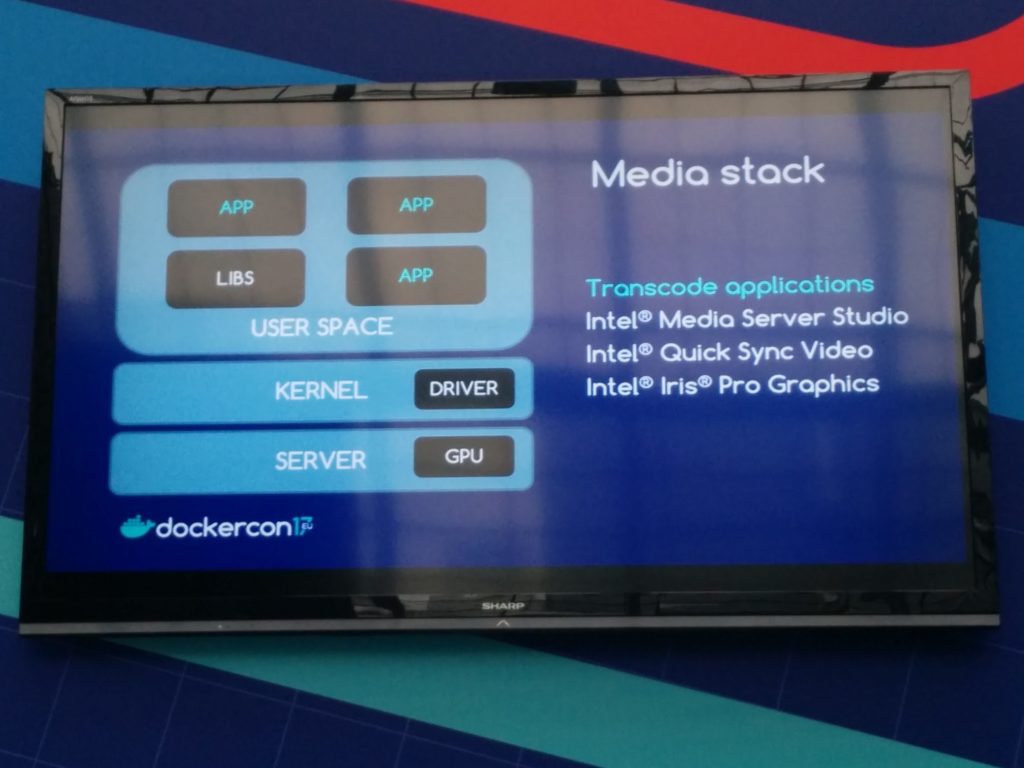
Chelsea began the talk with a quick intro to hardware accelerators (gpu, asic, fpga, etc.)
Then, she presented the Media Stack she used (her use case was video files conversion, using ffmpeg, relying on GPU hardware acceleration)
The Media Stack can be deployed using Docker as well
The container will have dependencies on the hardware and kernel modules; the speaker considered running several media stack apps in the same container or just one (preferred container deployment pattern), but the performance impact was negligible.
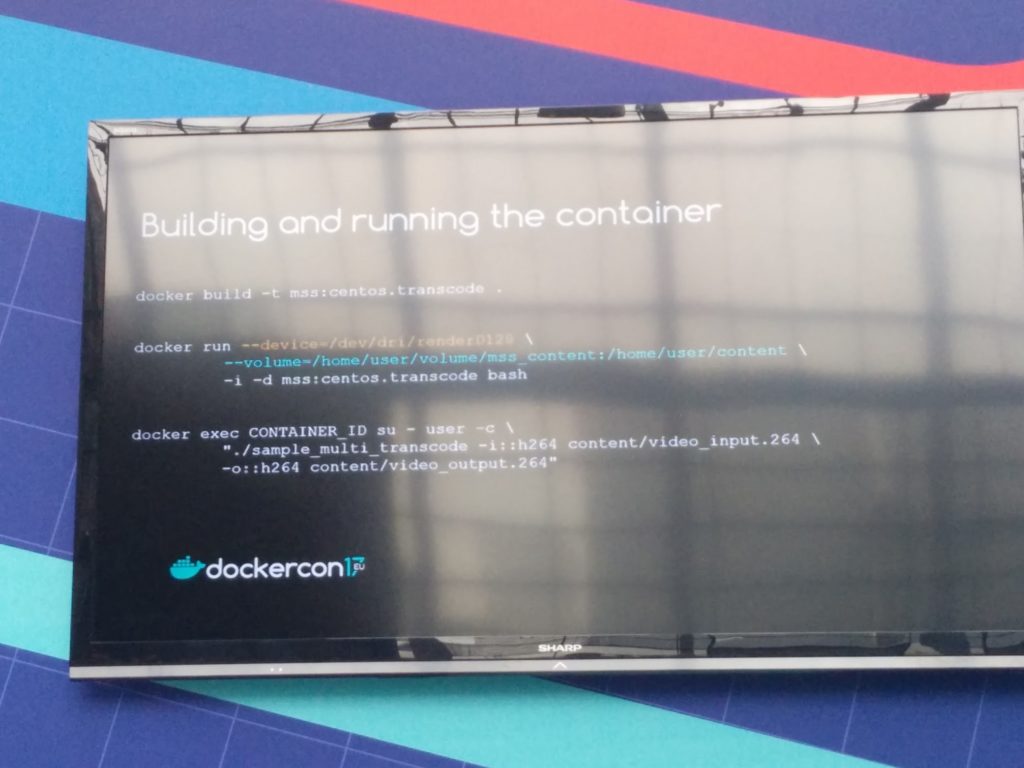
You can run the container specifying the particular device required or you can give it additional capabilities.( If the driver allows several applications to run and use the hardware accelerator concurrently, then you can run several containers against it as well – running your process in a container or outside does not change a thing from a driver / kernel perspective)
Your orchestration tool could understand hardware requirements; so could be worth it to use docker compose files to deploy the media stack.
Of course, such containers aren’t portable (since they require special hardware AND special kernel features / drivers from the Docker host), hence they’re pretty difficult to run…
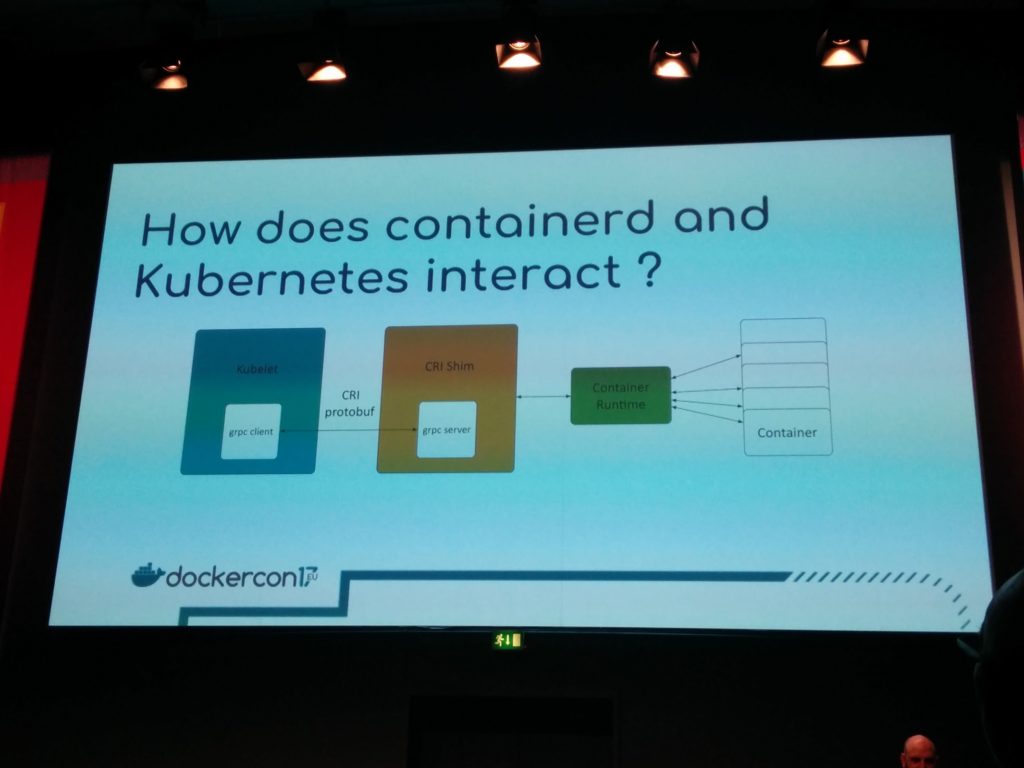
Looking under the hood : containerd by Scott Coulton
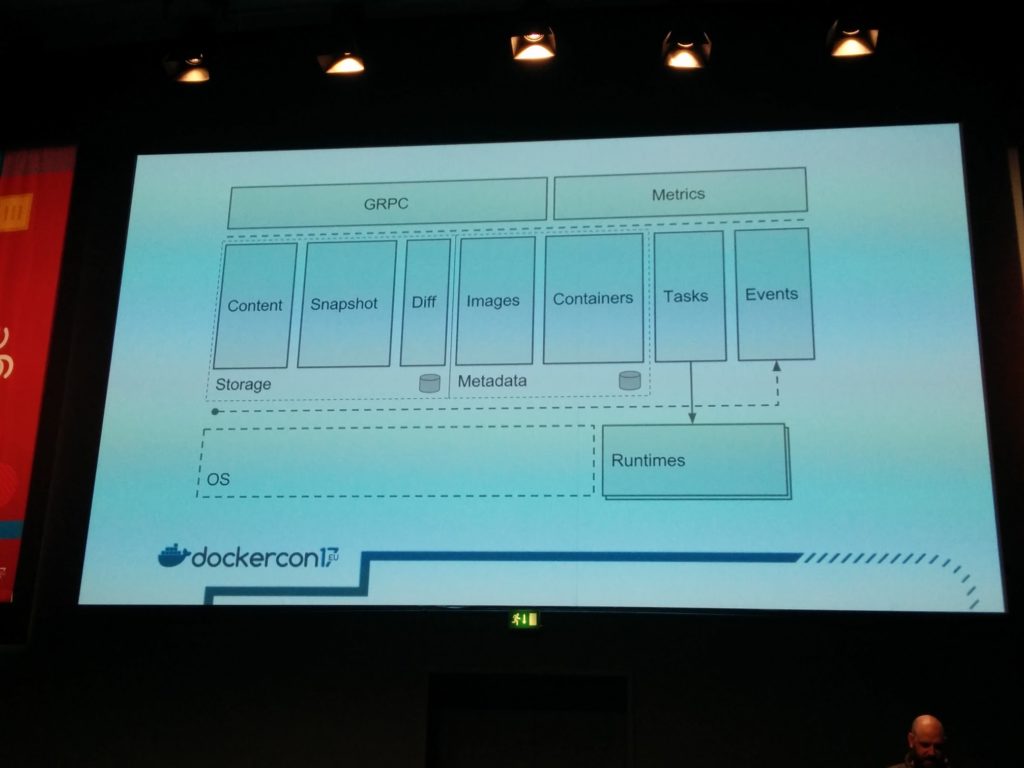
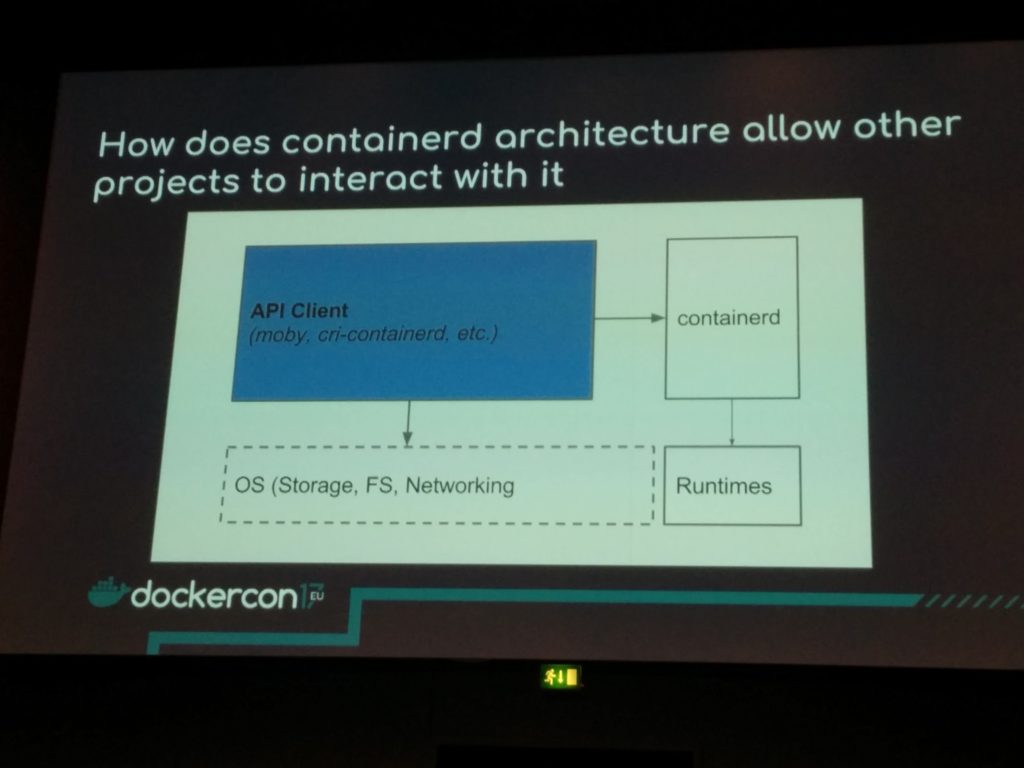
containerd is the industry standard for container runtimes (docker engine and kubernetes use it – it’s the component that will handle the containers lifecycle)
The container CLI (ctr) communicates with a daemon exposing a gRPC API over a unix sock and protobuffs.
Demo : we can pull directly from ctr pull and run an image, without docker installed, just containerd
Who uses containerd ? The Moby Project: the docker engine, swarmkit, hyperkit, runc, linuxkit plug into containerd.
Demo : we can run docker on top of containerd
The speaker then talked about linuxkit : it’s a lean , minimal size OS.
At Puppet, they made sure to only ship necessary packages in their linux image built from linuxkit.
linuxkit is also immutable, and its init is very basic : initd, runc, containerd and certificates are the only additional packages added to the linux image.
Demo : he built a linuxkit image with : moby build config.yml
What about kubernetes ? how does it interact with kubernetes ?
You can checkout the containerd kubernetes integration on github : https://github.com/kubernetes-incubator/cri-containerd
cri-o, rocketos are the competing runtimes, but their market share is super low. (1% maybe)
Taking Docker to production : what you need to know and decide by Brett Fisher
This talk was very well attended (200+ people) and pretty entertaining, thanks to a quizz on 80’ies video games being run along the talk, nice idea !
Brett basically told the audience to be pragmatic when Modernizing Traditional Apps (MTA) to Docker.
Limit your simultaneous innovation (aka scope creep) : is it necessary to have CI/CD on day one ? to containerize everything ? to persist data ? to allow dynamic performance scaling ? Also remember it’s not required to switch to micro services
First focus : Dockerfile and Dockerfile anti patterns
- trapping data (keeping data into the container) ; you need to use volumes when your app stores data
- Never use latest ! Same thing for packages installed via package manager, for critical packages, pin versions (apk add bash@VERSION)
- don’t leave the default config, use one with sane settings for a container run.
- don’t copy config at image build, use an entry point to overwrite per environment config (from env variables)
Deployment
Where to deploy ? VM or bare metal ?
As you wish – choose what you’re most comfortable with.
Visit bretfisher.com/dockercon17eu to read a white paper with a MySQL benchmark (comparison of performance across different container deployment scenarios)
Linux Distribution / kernel
The Linux distribution of your host does not matter that much; but make sure to use most recent kernels.
Not sure ? Ubuntu 16.04LTS , popular very well tested with Docker, wide storage driver support.
Or build your own linuxkit !
Swarm
- start with baby swarm : 1-node ; it will already give you more features (services that can heal, etc.)
- then HA swarm : 3-Node
- finally biz swarm 5-Node
Don’t turn cattle into pets : there should be no special container (meaning you should not have containers that can’t be replaced without affecting the system).
Multiple Swarms ?
Consider Outsourcing your plumbing
- don’t build your own image registry, there are plenty of them out there (Nexus3, Artifactory, Docker Trusted Registry, etc.)
- logs : some people use Elastic Search to store their logs (provided all your container logs go to sysout / syserr !)
- monitoring and logging : you can have a look at the Cloud Native Computing Foundation (cncf) webpage about tools : http://github.com/cncf/landscape
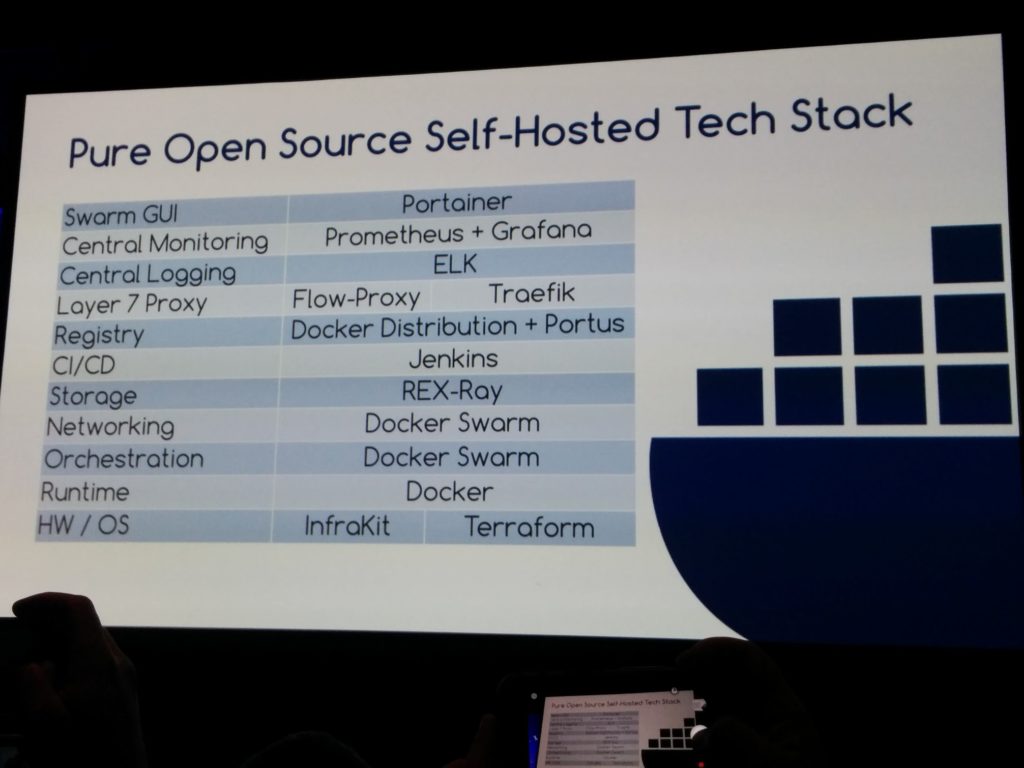
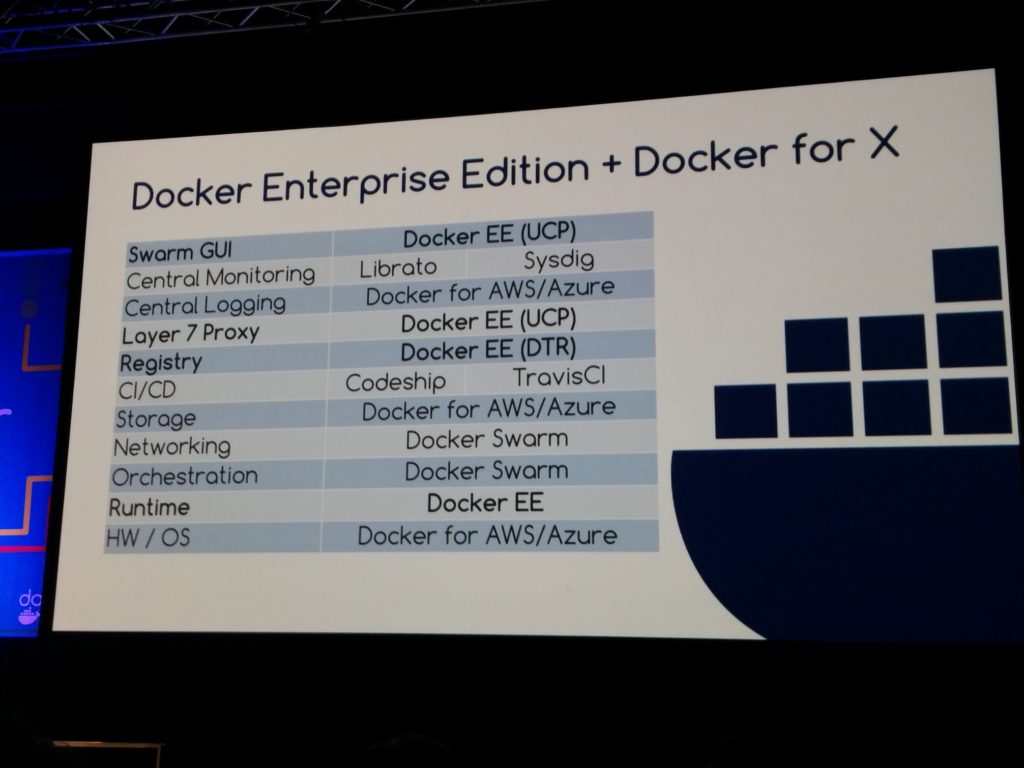
Tech stacks
Full opensource stack
Docker EE stack
You could also consider having just 1 container per VM, at least to start and explore how your software behaves.
Final notes / the end !
Docker inc. was clearly pushing its EE offering and partnerships (I guess there’s a time when startups need to make money) – nevertheless the technical content was very solid and interesting (containerd, linuxkit, play with docker, kubernetes integration, best practices for containerization, several use cases). Also many Docker engineers were available and happy to talk ! Many thanks to David Gageot, Guillaume Tardif, Guillaume Rose, Marcos Lilljedahl and others for their time and insights !)
Interestingly enough the community theater track (not in a room, a hundred seats or so at the end of the hallway) was full of great content from speakers from different horizons and companies such as Intel (hardware accelerating talk), CERN (crazy scale with million of containers, implementing their own layered file system, CernFS) and PlayWithDocker (PWD)
Most booths were about solutions around Docker (registries, security scanners, monitoring and logging, deployment, cloud providers)
We were a few SoftwareAG employees also running a booth there, it was interesting to meet SoftwareAG products users (Adabas, Aris, Apama, etc, and Terracotta Ehcache of course) currently working on containerization; we also celebrated the launch of several of our products on DockerStore, check them out !










thanks Anthony, appreciate the cogent summary..